Programmatic Remediation in Linux
Overview
In this lab, I will demonstrate how to establish a baseline scan of a Linux machine, intentionally create vulnerabilities, and then automate the remediation of those vulnerabilities using bash scripts.
Tools Used
Cloud Platform: Azure
Vulnerability Scanner: Tenable
Compliance Standard: Linux DISA STIG
VM: Linux Ubuntu
Applications: Bash, OpenSSL, Telnet
Create an Authenticated Scan in Tenable
Create a Scan in Tenable
Choose “User Defined” and Select “Linux - Vulnerabilities + DISA STIG”
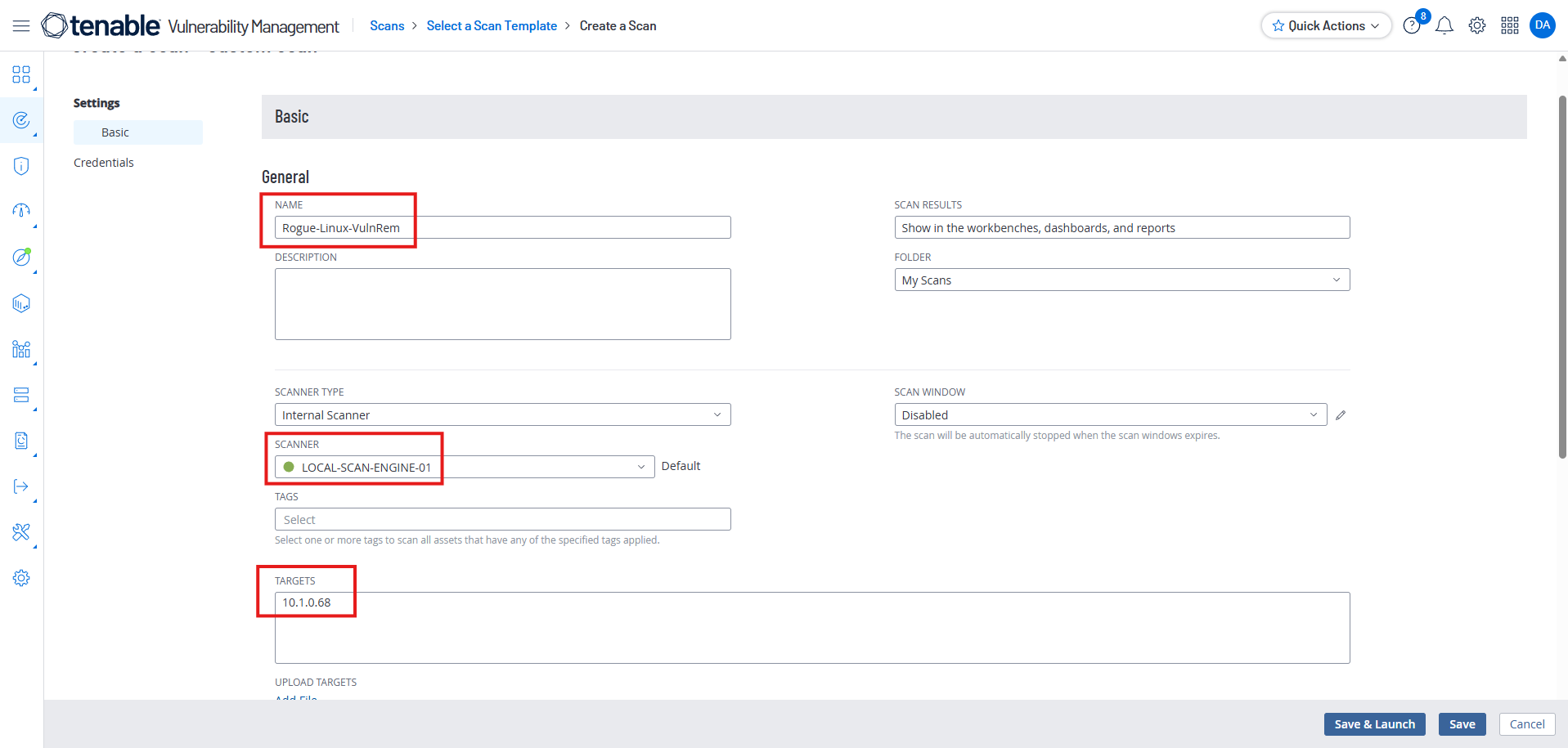
Name the scan, choose “LOCAL-SCAN-ENGINE-01” as the scanner, and use the VM’s internal IP address as the target.
Click on the Credentials blade, then Add Credentials, and choose Host
Then choose SSH
In Authentication Method, select password. Enter the username and password. For Elevate Privileges With, select su. Enter your username and password again in the SU LOGIN and ESCALATION PASSWORD fields. Then click on Save.
Conduct the Initial Scan
Now, Click on Save & Launch.
Intentionally Make Your VM Vulnerable
Log into the VM via SSH:
1
ssh rogueuser@[IP]
Install Telnet
1
2
3
4
5
sudo apt update
sudo apt install telnetd -y
sudo systemctl enable inetd.service
sudo systemctl start inetd.service
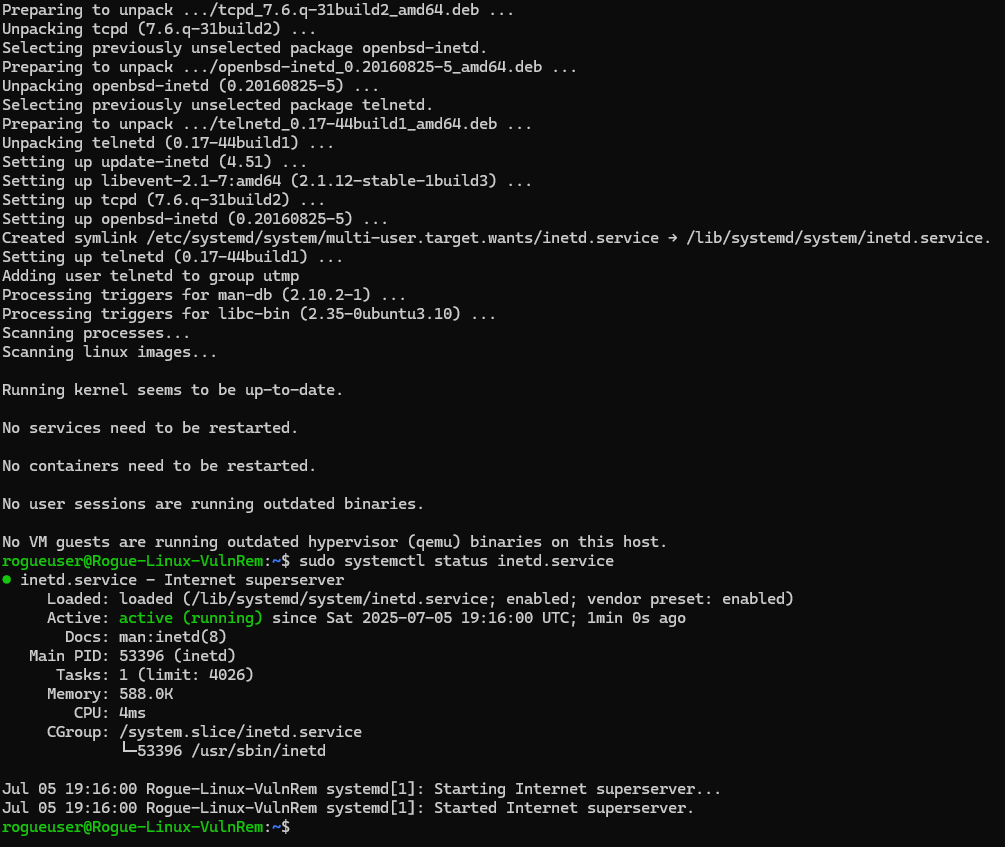
Check the status of the service
1
sudo systemctl status inetd.service
Enable Remote Root Login
Run the following commands to enable remote root login.
1
2
sudo grep -q '^PermitRootLogin' /etc/ssh/sshd_config && sudo sed -i 's/^PermitRootLogin.*/PermitRootLogin yes/' /etc/ssh/sshd_config || echo 'PermitRootLogin yes' | sudo tee -a /etc/ssh/sshd_config && sudo systemctl restart sshd
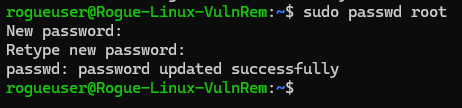
Set root password to “root”
1
sudo passwd root
Scan the VM again
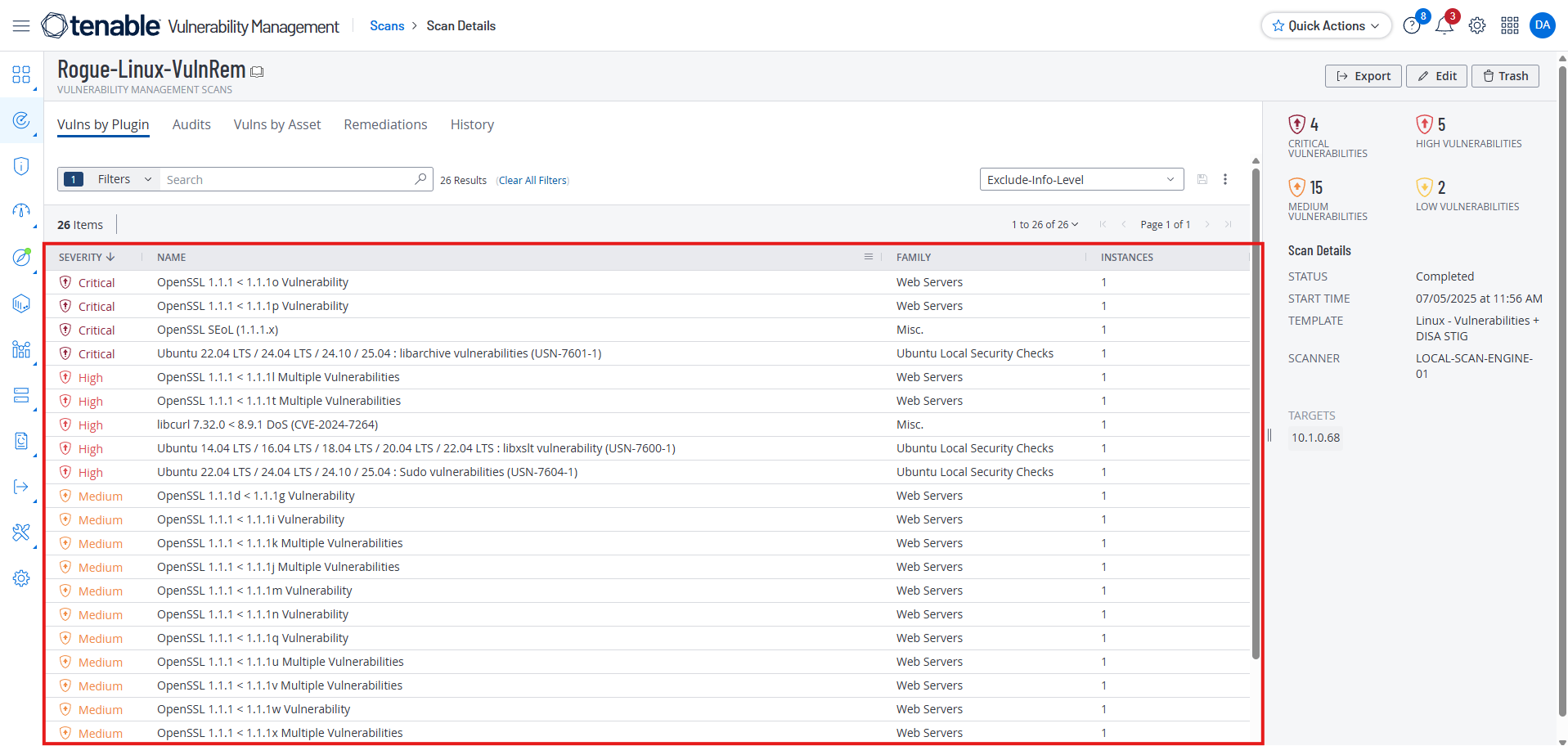
In our second scan results, we can see the vulnerabilities for the default password of “root” for the root account, the OpenSSL version vulnerabilities, and the unencrypted telnet server.
Remediate the Vulnerabilities
We will use the following scripts to remediate the three vulnerabilities.
Uninstall Telnet
lognpacific-public/automation/remediation-Telnet-Remove.sh at main · joshmadakor1/lognpacific-public
FILE: remediation-Telnet-Remove.sh
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
#!/bin/bash
# Stop the inetd service
sudo systemctl stop inetd.service
# Disable the inetd service to prevent it from starting at boot
sudo systemctl disable inetd.service
# Remove the telnetd package completely, including its configuration files
sudo apt remove --purge telnetd -y
# Remove the inetutils-inetd package completely, including its configuration files
sudo apt remove --purge inetutils-inetd -y
# Remove any unused dependencies that were installed with telnetd or inetutils-inetd
sudo apt autoremove -y
# Update the package lists to ensure they are current
sudo apt update
# Download the script
# wget https://raw.githubusercontent.com/joshmadakor1/lognpacific-public/main/automation/remediation-Telnet-Remove.sh --no-check-certificate
# Make the script executable:
# chmod +x remediation-Telnet-Remove.sh
# Execute the script:
# ./remediation-Telnet-Remove.sh
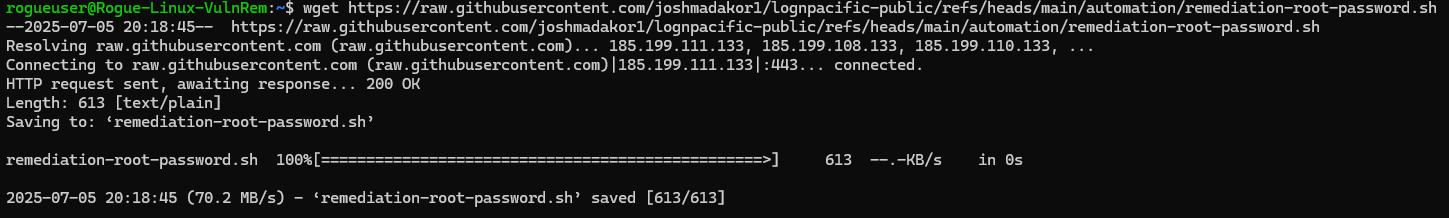
Download the script
1
wget https://raw.githubusercontent.com/joshmadakor1/lognpacific-public/refs/heads/main/automation/remediation-Telnet-Remove.sh
Add execution rights to the script once it is downloaded:
1
chmod +x remediation-Telnet-Remove.sh
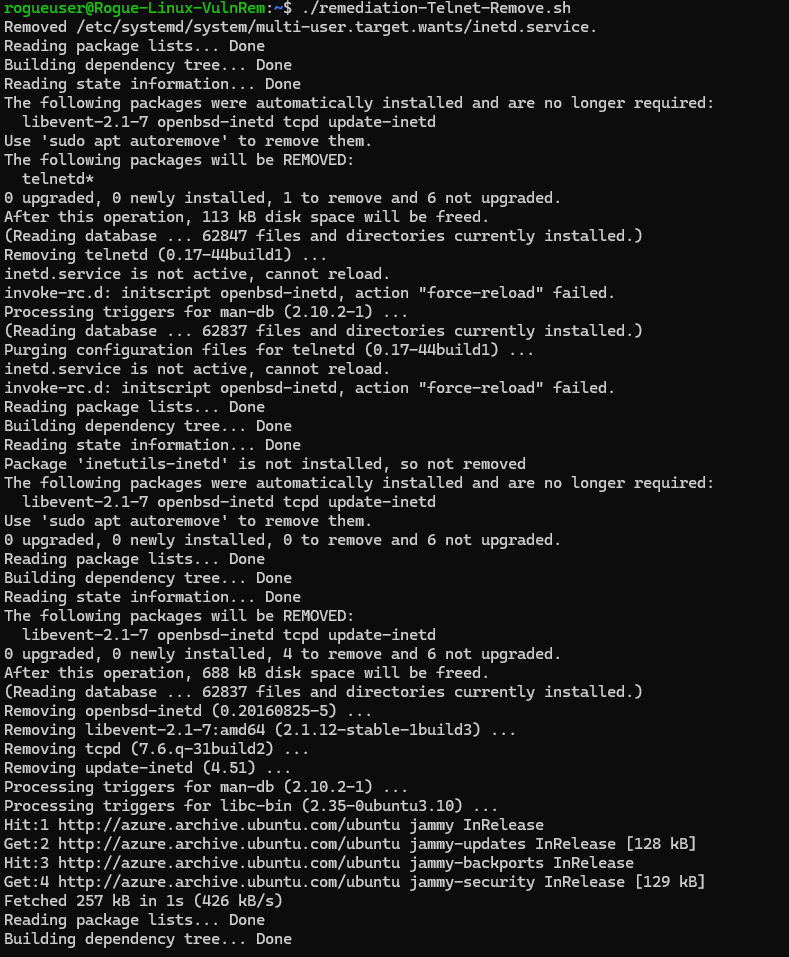
Run the script
1
./remediation-Telnet-Remove.sh
Change Root Password from Default
lognpacific-public/automation/remediation-root-password.sh at main · joshmadakor1/lognpacific-public
FILE: remediation-root-password.sh
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
#!/bin/bash
echo -e "Cyberlab123!\nCyberlab123!" | sudo passwd root
# This will delete the file after you're done so it doesn't store the password on the local system
# There are better ways to go about this, but this is just a proof of concept to remediate this particular vulnerability.
rm remediation-root-password.sh
# Download the script
# wget https://raw.githubusercontent.com/joshmadakor1/lognpacific-public/main/automation/remediation-root-password.sh --no-check-certificate
# Make the script executable:
# chmod +x remediation-root-password.sh
# Execute the script:
# ./remediation-root-password.sh
Download the script
1
wget https://raw.githubusercontent.com/joshmadakor1/lognpacific-public/refs/heads/main/automation/remediation-root-password.sh
Add execution rights to the script
1
chmod +x remediation-root-password.sh
Execute the script
1
./remediation-root-password.sh
Update OpenSSL to version 3.0.5
FILE: remediation-openssl-3.0.5-install.sh
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
#!/bin/bash
echo "Installing dependencies..."
sudo apt update
sudo apt install build-essential checkinstall zlib1g-dev -y
# Download and extract OpenSSL 3.0.5
echo "Downloading and extracting OpenSSL 3.0.5..."
sudo wget -P /usr/local/src https://www.openssl.org/source/openssl-3.0.5.tar.gz
cd /usr/local/src
sudo tar -xf openssl-3.0.5.tar.gz
# Compile and install OpenSSL
echo "Configuring, compiling, and installing OpenSSL..."
cd openssl-3.0.5
sudo ./config
sudo make
sudo make install
# Set library path for OpenSSL libraries
echo "Setting library paths..."
echo "/usr/local/lib64" | sudo tee /etc/ld.so.conf.d/openssl-3.conf
sudo ldconfig
# Confirm the installation
echo "Installation confirmed with the following version:"
/usr/local/bin/openssl version
# Reboot to apply all changes
echo "Rebooting system to apply changes..."
sudo reboot
# Download the script
# wget https://raw.githubusercontent.com/joshmadakor1/lognpacific-public/main/automation/remediation-openssl-3.0.5-install.sh --no-check-certificate
# Make the script executable:
# chmod +x remediation-openssl-3.0.5-install.sh
# Execute the script:
# ./remediation-openssl-3.0.5-install.sh
Download the script
1
wget https://raw.githubusercontent.com/joshmadakor1/lognpacific-public/refs/heads/main/automation/remediation-openssl-3.0.5-install.sh
Add execution rights to the script
1
chmod +x remediation-openssl-3.0.5-install.sh
Run the script
1
./remediate-openssl-3.0.5.install.sh
At the end of the script, the script causes the VM to restart, so your SSH connection will become disconnected.
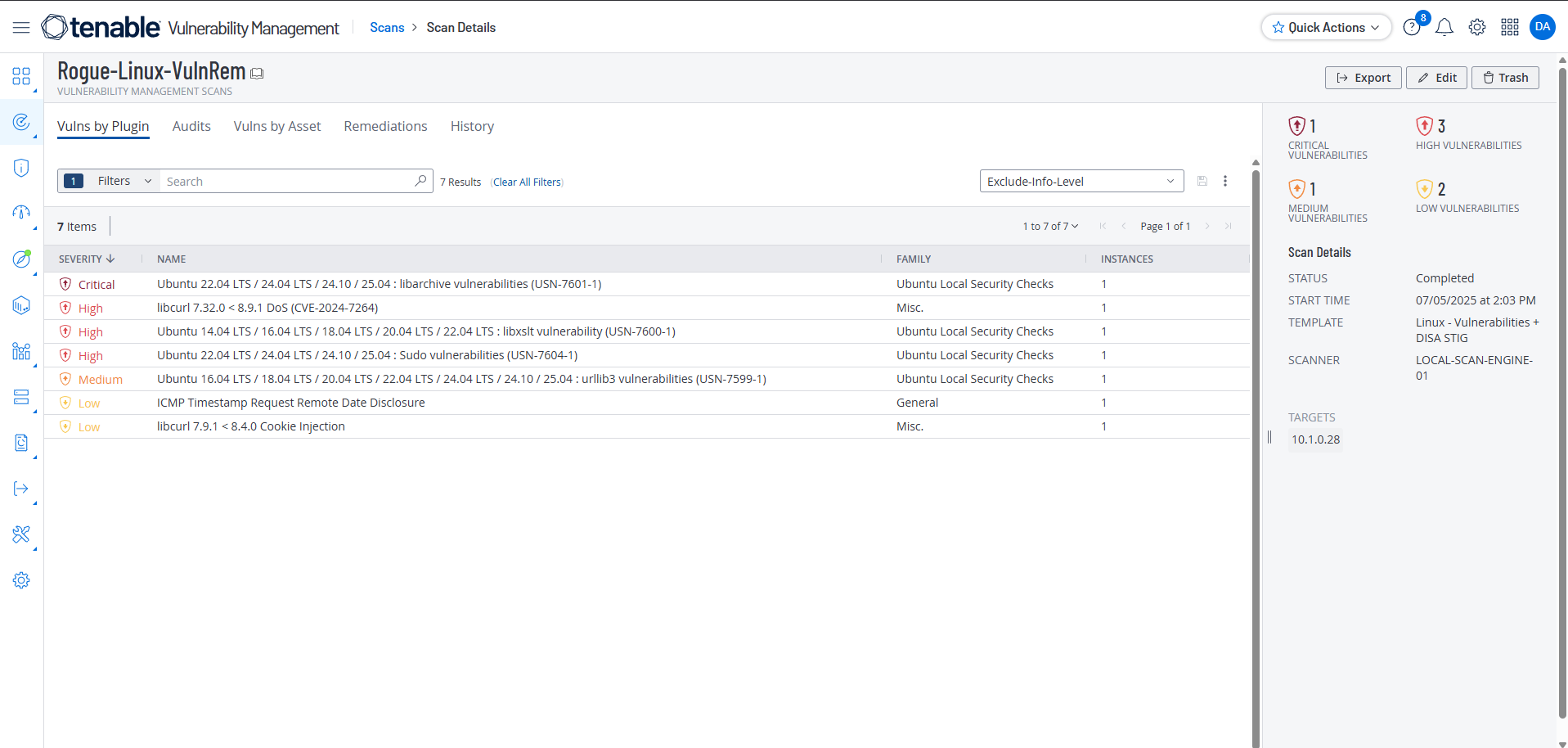
Scan the VM after Remediation
The scan results indicate that the vulnerabilities that we had created - the default root password of “root”, the vulnerable telnet server, and the vulnerable version of OpenSSL - have all been remediated.
Conclusion
As you seen in the scans above, the intentionally created vulnerabilities have been remediated. Automating the remediations using bash scripts allows us to not only efficiently remediate these vulnerabilities, but allows the remediations to occur at scale and repeatedly if needed.